Server hack with Metasploit and Armitage (15 points)
What You Need for This Project
- Host Machine: A Windows (any version) computer with VMware
Player installed. If you are using the S214 lab, VMware Player is
already installed. If you are using some other computer, you can
download VMware Player here:
https://my.vmware.com/web/vmware/free#desktop_end_user_computing/vmware_player/5_0
You can use some other host OS if you like, such as Mac OS X or Linux, and if you prefer to use some other virtual machine software like VirtualBox, that's fine too. - Target Machine: You need the DVD that was handed out in class, which contains a Windows 2008 target virtual machine.
If you don't have the DVD, all you really need is a Windows machine with DEP set to "Turn on DEP for essential Windows programs and services only", the firewall turned off, and EasyFtp Server 1.7.0.11 from Here
- Attacker Machine: You need the DVD that was handed out in class, which contains a Kali Linux 2.0 virtual machine.
If you don't have the DVD, you can download Kali Linux here: http://www.kali.org/downloads/
Starting the Virtual Machines
As you did in the previous project, start both the Kali Linux and Windows Server 2008 virtual machines. Make sure they are both using Bridged networking. If you have problems with the virtual machines, refer to the previous project.Finding Your Target Virtual Machine's IP Address
Click Start, Run. Type in CMD and press the Enter key.In the Command Prompt screen, type in IPCONFIG and press the Enter key.
Write down your IP address.
Make sure both machines are in Bridged networking mode! The most common problem students have is incorrect networking modes. Unless otherwise specified, make sure all virtual machines you use in this class are in Bridged networking mode.
Turning off "Blank Screen" in Kali
By default, Kali 2.0 will keep locking the screen after a few seconds of inactivity, which is irritating. To fix this, on the left side of the Kali 2.0 desktop, click the bottom button to "Show Applications", as shown below. On the right side of the Kali 2.0 desktop, click the lowest circle to show the bottom screen.Then click Settings, as shown below.
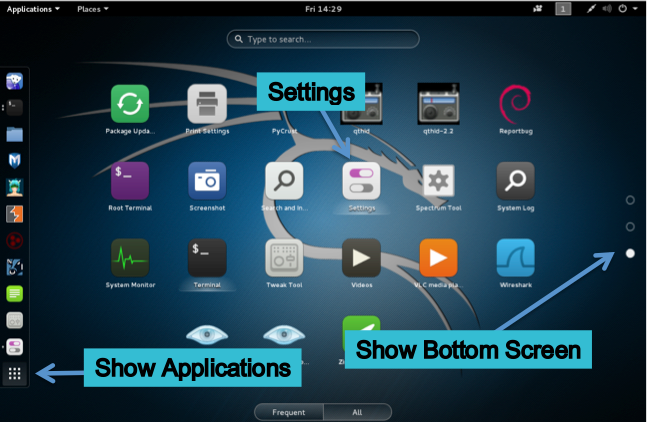
In the "All Settings" window, click Power.
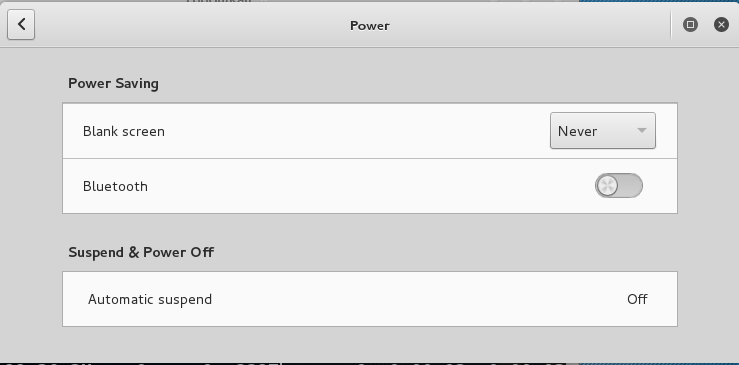
Set "Blank screen" to Never, as shown below.
Updating Kali
In a Terminal window, execute these commands:
apt-get update
apt-get upgrade
apt-get dist-upgrade
Starting Armitage on Kali Linux
To start Armitage, in a Terminal window, execute these commands:
msfdb init
armitage
In the "Connect..." box, accept the default values and click the
Connect button.
In the "Start Metasploit?" box, click the Yes button.
Armitage opens, as shown below.
Troubleshooting
If the "Progress" box times out and cannot connect, try this:
Scanning for Targets
In Armitage, click Hosts, "Nmap Scan", "Intense Scan". A box pops up saying "Enter scan range (e.g., 192.168.1.0/24):". Type in your target machine's IP address with a /32 added to the end of it, as shown below. Click the OK button.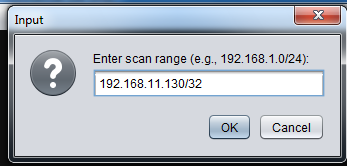
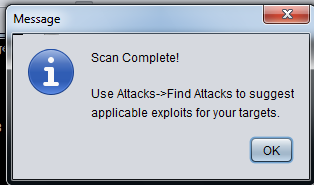
The scan will take a few minutes. When the scan is done, a box pops up saying "Scan Complete!", as shown below. Click OK.
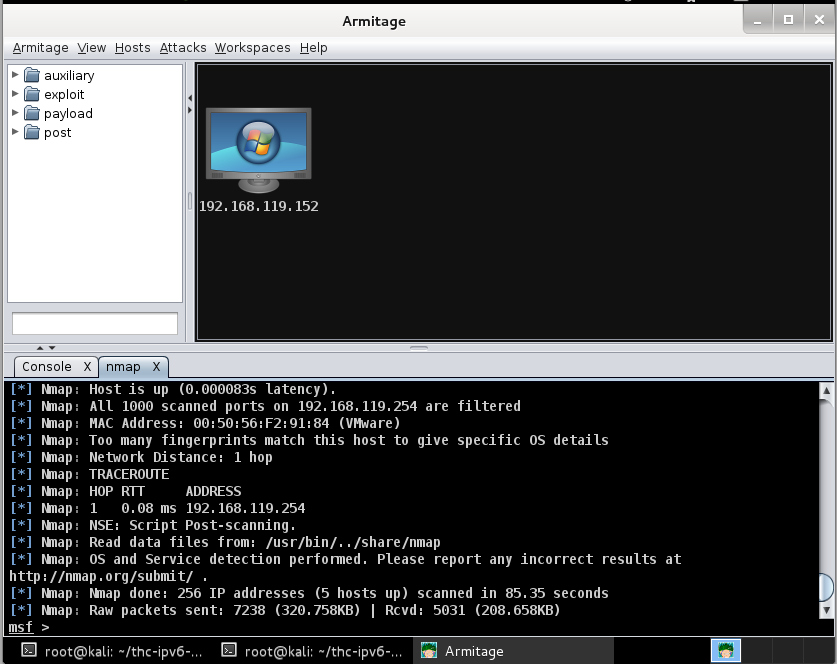
The target machine appears in the upper center part of the Armitage window, with a Windows logo on it:
Exploiting the Target with the easyftp_cwd_fixret Attack
In the upper left pane of Armitage, at the bottom, type in easyftp Several exploits appear, as shown below.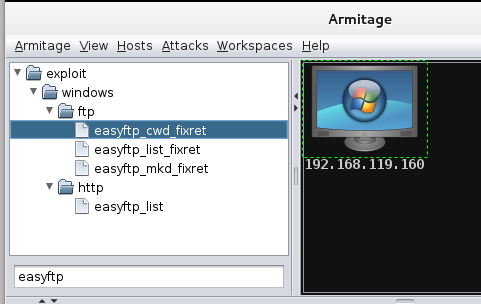
Click easyftp_cwd_fixret, hold down the left mouse button, drag it onto the computer icon showing your target's IP address, and drop it there.
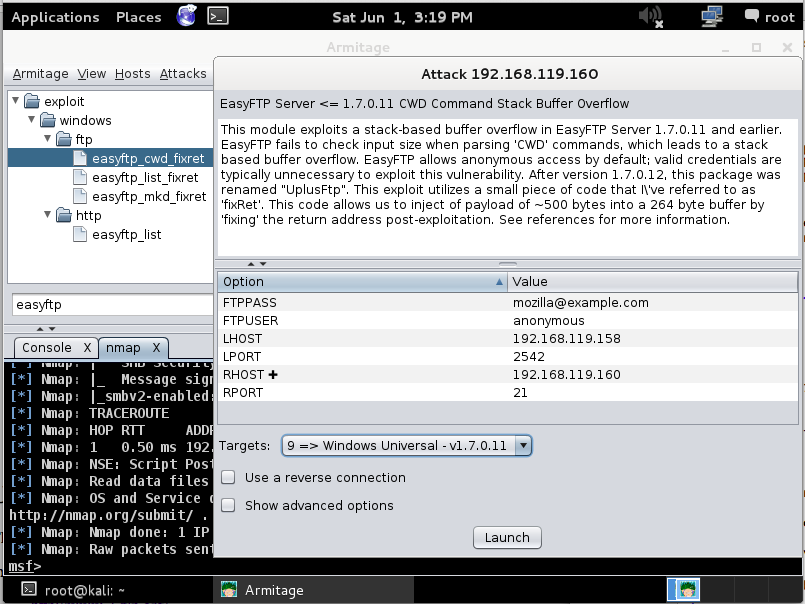
An Attack box pops up with details about the attack.
At the bottom of this box, in the "Targets:" drop-down list box, select "9 => Windows Universal - v1.7.0.11", as shown below.
Click Launch.
When the attack succeeds, the bottom pane will show "Meterpreter session 1 opened", (or some other session number) as shown below.
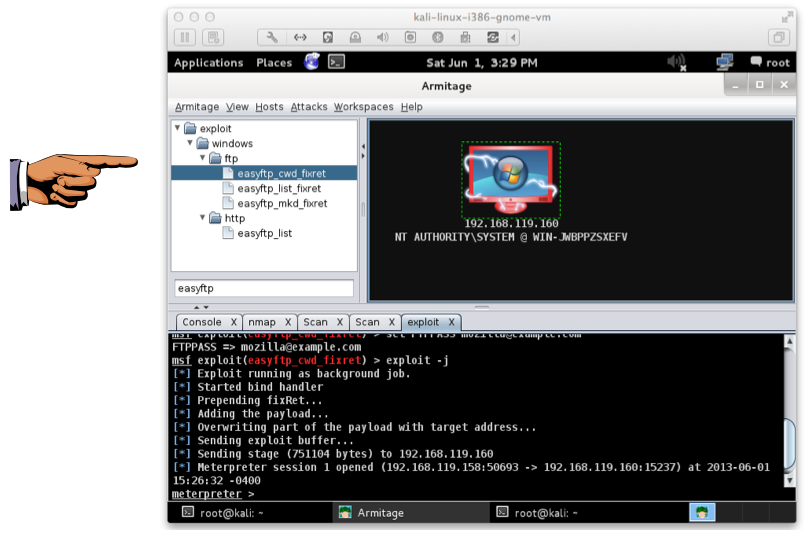
The target machine now shows electric arc graphics on it, indicating this box is owned!
Troubleshooting
If you see an error message saying "connection refused", that usually means the EasyFTP service crashed. It does that a lot. To fix it, on the Windows server, click Start, type in SERVICES, open the Services console, and restart the EasyFTP service. Then try the exploit again.
Saving a Screen Image
Make sure the electric arc around the target machine is visible in the upper pane of Armitage, demonstrating that you "own" the Target machine. Click the taskbar at the bottom of your host Windows 7 desktop, to make the host machine listen to the keyboard, instead of the virtual machine.Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
On the host machine, not the virtual machine, click Start.
Type mspaint into the Search box and press the Enter key.
Click in the untitled - Paint window, and press Ctrl+V on the keyboard. The desktop appears in the Paint window.
Save the document with the filename "YOUR NAME Proj 2a", replacing "YOUR NAME" with your real name.
Post-Exploitation
Now let's gather information from the target. Right-click the target computer icon, and click Meterpreter, Explore, Screenshot, as shown below.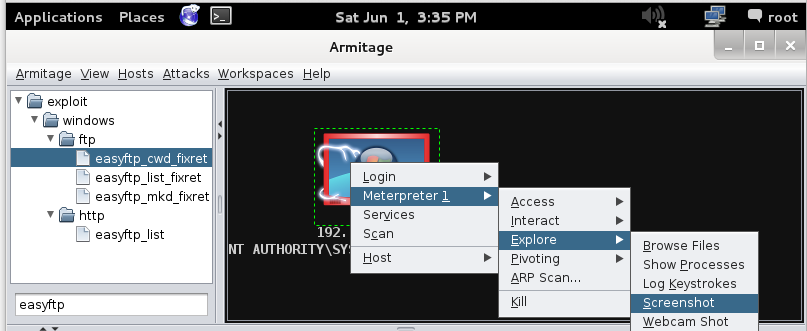
The Target machine's desktop appears in the lower pane of Armitage, as shown below.
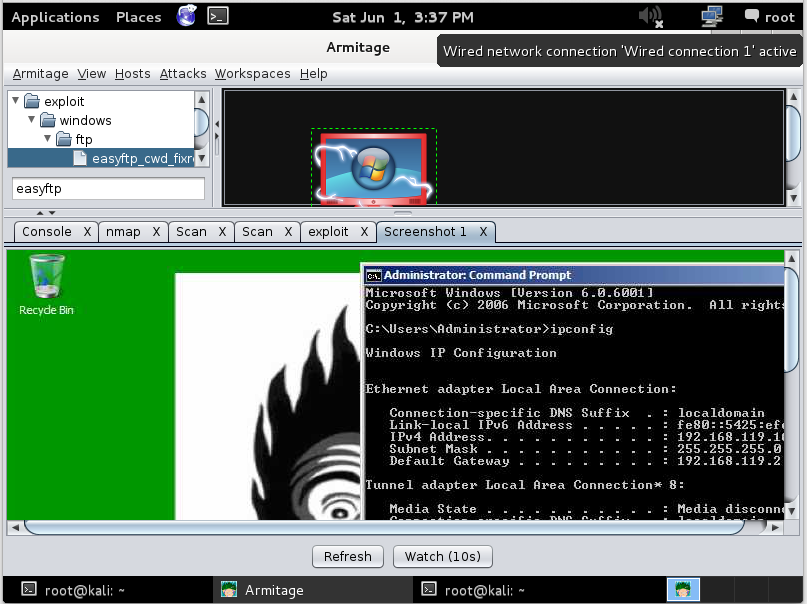
Hardening the Target Machine
To protect the Target from this attack, we will turn Data Execution Protection (DEP) back on. DEP prevents buffer overflow attacks like this, even if someone is foolish enough to install old, buggy software. In the Target Machine, click Start, right-click Computer, and click Properties.In the System window, in the left portion, click "Advanced system settings".
In the "System Properties" sheet, click the Advanced tab, as shown below:
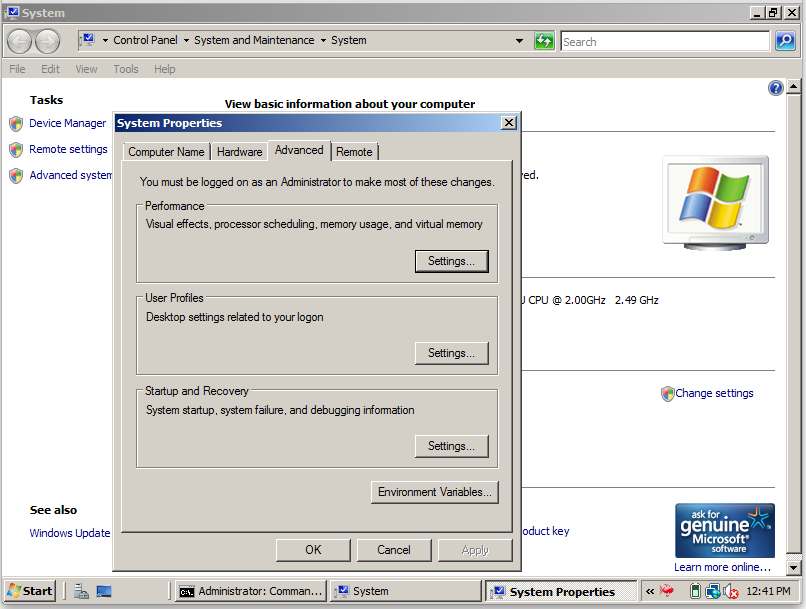
In the "Performance" section, click the Settings button.
In the "Performance Options" box, click the "Data Execution Prevention" tab.
Click the "Turn on DEP for all programs and services except those I select:" radio button, as shown below:
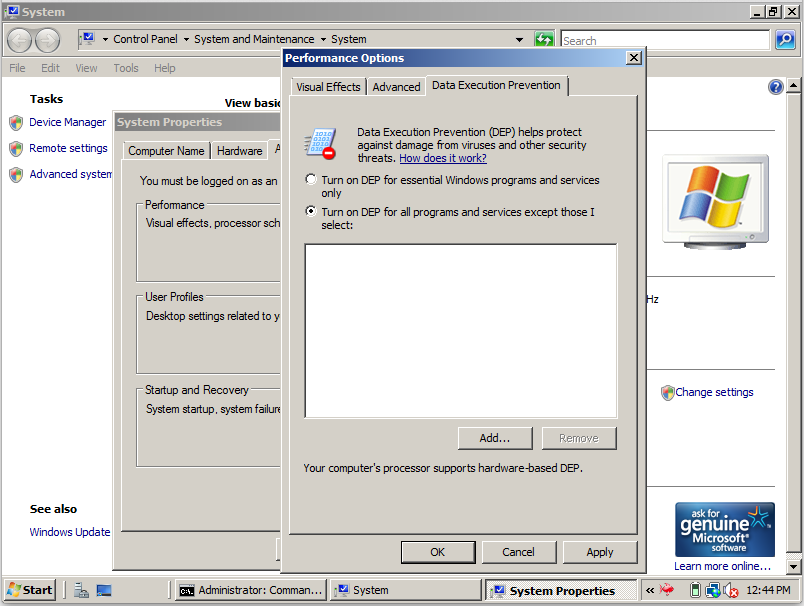
Click OK. Click OK. Click OK. Restart your Target machine.
Troubleshooting
If you see a message at the bottom of this box saying "Your hardware does not support DEP", this indicates either that your computer is very old, or, far more likely, DEP is disabled in the BIOS. Close all windows and restart the machine. Press the function key to get into the BIOS and enable DEP before proceeding.
Log in as Administrator with a password of P@ssw0rd
Launching the easyftp_cwd_fixret Exploit Again
In Armitage, drag easyftp_cwd_fixret onto the computer icon showing your target's IP address, and drop it there. An Attack box pops up with details about the attack.At the bottom of this box, in the "Targets:" drop-down list box, select "9 => Windows Universal - v1.7.0.11".
Click Launch.
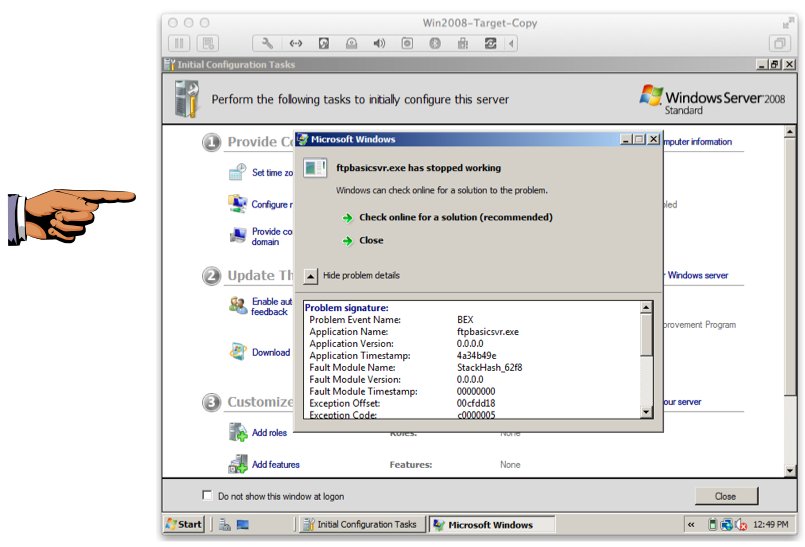
On the Windows target's desktop, a "Microsoft Windows" button starts blinking at the bottom of the screen.
Click the "Microsoft Windows" button
A "Microsoft Windows" box appears, with the message "ftpbasicsvr.exe has stopped working", as shown below.
DEP has saved your server by stopping the attack!
Saving a Screen Image
Make sure the "Sftpbasicsvr.exe has stopped working" message is visible, as shown above. Click the taskbar at the bottom of your host Windows 7 desktop, to make the host machine listen to the keyboard, instead of the virtual machine.Press the PrintScrn key in the upper-right portion of the keyboard. That will copy the whole desktop to the clipboard.
YOU MUST SUBMIT A FULL-SCREEN IMAGE FOR FULL CREDIT!
On the host machine, not the virtual machine, click Start.
Type mspaint into the Search box and press the Enter key.
Click in the untitled - Paint window, and press Ctrl+V on the keyboard. The desktop appears in the Paint window.
Save the document with the filename "YOUR NAME Proj 2b", replacing "YOUR NAME" with your real name.
Turning in Your Project
Email the images to me as attachments to an e-mail message. Send it to: cnit.123@gmail.com with a subject line of "Proj 2 From YOUR NAME", replacing "YOUR NAME" with your real name. Send a Cc to yourself.Sources
Last Modified: 2-4-16
No comments:
Post a Comment