The
notion of the “ethical hacker” has always been an ironic one. The
developing trends of ethical hacking and offensive security have
transformed the information security industry into one of the most
self-perpetuating industries in the world.
The
software and tools that are used to secure vulnerable information
assets are the same tools that can be used to exploit them. Perhaps it’s
the other way around. Perhaps the tools that were created for the sole
purpose of exploiting information assets are now being used to safeguard
them. I suppose this is a debate that could go on forever and is really
just another instance of “what came first…the chicken or the egg?”
The
purpose of this essay is not to discuss the philosophical question of
intent. My intentions are more modest. I merely seek to justify the
importance of a tool that has been consistently labeled as malicious
hacking software. The tool that I am referring to is Network Mapper, or
nmap for short. Whether you are a crazed rogue agent that is bent on
inciting global revolution or a network security professional (hopefully
the latter, rather than the former), nmap should have a permanent place
in your toolkit. Perhaps, instead of hurling criticism at an extremely
functional networking tool, we should hold individuals accountable for
their actions and reflect upon the well-known Benjamin Parker
caveat…“with great power, comes great responsibility.” Despite some
claims to the contrary, nmap is not malicious software. And I think the
only reason that it is often labeled as such is because of its very
impressive list of capabilities. Despite its potential to do harm, nmap
can certainly play an important role in securing a network
infrastructure within a professional environment.
Nmap
has steadily evolved over the years from a simple scanning utility into
a full blown penetration testing platform. It can be used in every step
of the security auditing process, to include network discovery, port
scanning, service enumeration, vulnerability mapping and even
exploitation. Throughout this article, I will discuss the capabilities
of nmap as they pertain to each step in the penetration testing process.
Installation and Preparation
Obviously,
prior to using nmap, it is important to have a functional version
installed on the system that you are using. By default, nmap is already
installed on most penetration testing and network security operating
systems such as Kali-Linux, Backtrack, DEFT, Node-Zero, Security Onion
and NST. However, it can also be loaded to nearly any platform of your
choice. Nmap can easily be installed on all commonly used operating
systems to include Windows, Linux and OSX. There is also documentation
available for installing it on more obscure platforms to include BSD,
Solaris, AIX and AmigaOS. Installation packages and instructions on how
to perform the install on any of these systems can be found at http://nmap.org/book/install.html.
Zenmap – Graphical Interface
In
addition to the traditional command-line interface for nmap, there is
also a graphical front-end interface called Zenmap. Zenmap is also
integrated into many of the different penetration testing platforms
previously discussed. However, it is not installed by default in
Kali-Linux (the platform that I will be using for this tutorial).
Fortunately, it is in the installation repository and can easily be
installed with a single command:
apt-get install zenmap
Zenmap’s
point-and-click interface not only effectively streamlines what would
otherwise require complicated commands but it can also be an extremely
useful tool for learning how to use nmap. It uses ‘profiles’ to save
commonly used scan configurations for later modification and/or use.
Take a look at the image of the Zenmap interface that is provided in
Figure 1 and we will briefly address each of the components.
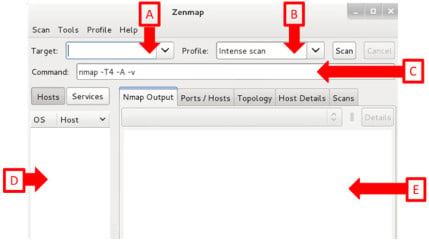
Figure 1. Zenmap Graphical Interface
The
first component is the Target field (Figure 1. A). This field is where
you can specify the remote systems that you want to run a scan against.
You can enter a single IP address (e.g. 192.168.1.1), you can enter a
sequential range of IP addresses (e.g. 192.168.1.0-255) or you can use
CIDR notation to specify a desired subnet (e.g. 192.168.1.0/24). The
second component is the Profile field (Figure 1. B). You can click on
the drop down arrow to the right of this field to see several
pre-configured profiles for scanning. Profiles allow you to save
commonly used scan configurations for future use. You can also create
profiles of your own and they will then appear in this list (we’ll
discuss how to do this later in this article). The third component is
the Command field (Figure 1. C). This field will indicate the command
that is going to be sent to the backend. To launch the command appearing
in this field, you simply click the Scan button. You can modify the
value in this field directly; however, it will be automatically
populated based on the values of the Target field and the selected
profile. If you are new to nmap, you should pay close attention to this
field, as it will provide you with a better understanding of the
appropriate syntax and use of different nmap commands. The fourth
component is the Host/Service list (Figure 1. D). Once you have
performed scans, information will be populated in this list. If you have
the Hosts button selected, all discovered host IP addresses will be
listed. And if you have the services button selected, all discovered
network services will be listed. The final component (Figure 1. E) is
where you can sort through all of the information that has been produced
by all the scans that you have performed. The Nmap Output tab will
display the exact output that would be provided if the command had been
entered from the command-line interface. The Ports/Hosts tab content
will vary depending on if you have the Hosts or Services button selected
for your list. If the Hosts button is selected, then the information
under the Ports/Hosts tab will reflect the services that were identified
on the actively highlighted IP address in the list. Otherwise, if the
Services button is selected, the information under the Ports/Hosts tab
will identify all hosts that were found to have the particular service
that is highlighted in the list. The topology tab will provide a
graphical representation of the logical topology of the network, to
include all hosts that have been discovered by scanning. It will use
returned TTL (Time-To-Live) values to display the logical orientation of
hosts, relative to one another. The Host Details tab is where you will
find the bulk of information that has been discovered about a selected
host. This information includes MAC addresses, IP addresses, open ports,
identified services, operating system information and any additional
information that has been collected. Finally, the scans tab will provide
a history of scans that have been performed during the session.
At
the top of the screen you will see several different drop-down menus to
include Scan, Tools, Profile and Help. The Help menu is
self-explanatory. The Scan menu contains options to create new scans,
save scans or open previously saved scans. The Tools menu provides some
additional functions that can be used to sort through and organize
information collected during your scans. And the Profile menu provides
options to create new scan profiles or edit existing profiles.
We
will now briefly discuss how to create a new profile and then launch a
scan using that profile. To get started, select the Profile drop-down
menu and then select “New Profile or Command.” This will open up a
profile configuration interface that can be seen in Figure 2.
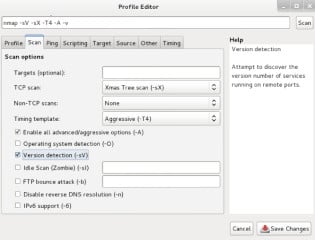
Figure 2. Zenmap Profile Editor
The
first tab (Profile tab) allows you to create a unique name and
description for the profile. All the other tabs are where you will
specify different configurations that will be used in your scan. As you
can see in the Scan tab displayed in Figure 2, creating a scan profile
is as simple as checking the boxes for options that you want to enable,
entering values so that those options can be effectively employed, or
selecting from pre-defined choices in the drop-down menu. If you are
unsure about the function or appropriate use of any option here, you can
hover over it with your mouse and the help column on the right side of
the screen will be automatically populated with information on what the
specific option does and appropriate values and syntax for any requested
input fields. With each minor adjustment that you make to the scan
configuration, the command field at the top is adjusted accordingly.
This feature makes Zenmap an extremely effective tool in learning how to
use nmap commands correctly. Once you have configured the scan options
to your liking, you can either select the Scan button at the top right
of the screen for single use, or you can select Save Changes at the
bottom right. The Save Changes button will save the profile with the
name provided on the first tab configurations and can then be used
immediately or at a later time by selecting it by name from the Profile
drop down menu on the main Zenmap interface. Although Zenmap is very
powerful, you should not allow it to become a crutch that prevents you
from learning the command line functions of nmap. Although Zenmap can
perform many of the same functions, it still has its limitations and is
not as powerful as nmap. To use nmap effectively and to its full
potential, it is important to become equally familiar with the command
line interface.
Network Discovery
The
first step in the penetration testing process that we are going to
discuss is network discovery. Prior to evaluating the security of
information systems on a network, you first need to identify what you
are evaluating. There are a number of different ways that you can
discover hosts on a network by using nmap. In this section, we will
discuss how to use nmap to perform host discovery at layers 2, 3 and 4
of the OSI model and we will also discuss the advantages and
disadvantages of each. An example of a command to perform layer 2
discovery can be seen here:
nmap -PR -sn 192.168.1.0-255
The
-PR
switch specifies an ARP ping. This uses layer 2 ARP (Address Resolution
Protocol) packets to identify live hosts within the specified range. It
does this by sending out an ARP broadcast request for each of the IP
addresses identified. If there is a live host on the network with one of
those IP addresses, that host will send an ARP reply to the scanning
system with its IP address and its corresponding layer 2 MAC address.
Nmap will collect replies from all live hosts and then will return a
list of hosts that were discovered. The -sn switch is used
to request nmap not perform any port scanning. This prevents the
transmission of any additional traffic, beyond what is necessary to
perform the layer 2 host discovery sweep. Layer 2 discovery is effective
because it is the fastest of all three options. However, it is limited
by the fact that it can only be performed against hosts that are on the
same local area network as the system that is performing the scan.
For
remote hosts, you will have to use either layer 3 or layer 4 discovery.
An example of a command that could be used to perform layer 3 discovery
is:
nmap -PE -sn 109.74.11.0-255
This
command will send a series of ICMP echo requests to each layer 3 IP
address in the list. Nmap will collect all ICMP echo replies that are
received and will return a list of all live hosts. This discovery scan
is slower than performing an ARP ping, but it will return results for
hosts on remote networks.
Finally,
suppose that you are attempting to discover remote systems (so you
can’t use layer 2) that are behind a firewall that drops all incoming
ICMP traffic (so you can’t use layer 3). To address this problem, you
will need to perform discovery at the transport layer (layer 4). There
are several different ways that you can use layer 4 scans to perform
discovery. One effective method is using a UDP ping. An example of a UDP
ping command is:
nmap -PU53 -sn 109.74.11.0-255
This
command generates a series of DNS server status requests for each of
the target IP addresses. A series of DNS query responses will be
received from live hosts and nmap will then return these results.
Because DNS is a commonly used service on UDP port 53, it is possible to
identify additional live hosts by using this technique that may have
been configured to not respond to ICMP traffic. Another effective layer 4
alternative to ICMP ping sweeps is to use a TCP ACK ping. An example of
this can be seen below:
nmap -PA80 -sn 109.74.11.0-255
This
command will send a series of unsolicited ACK replies to the specified
port for all of the hosts in the IP range. Because these ACK packets
were out of context of any established line of communication, live hosts
will reply with a TCP RST packet to indicate that the communication
should be discontinued. Nmap will collect these responses as the
indication of live hosts and will then return a list of them.
Port Scanning and Service Enumeration
Now
that we have discovered the active IP addresses on the network that we
are performing a penetration test against, we next need to identify open
ports on each system and the services running on those ports. Scanning
TCP ports on remote systems is the most basic function of nmap. To
perform a TCP scan of a target system, use the basic command:
nmap 109.74.11.34
Like
other nmap commands, this can also be used to perform scans against
multiple hosts by using a sequential series (192.168.1-255) or CIDR
notation (192.168.1.0/24). This standard nmap command performs a scan on
1000 commonly used TCP ports. Alternatively, you can specify a single
port to scan by using the -p switch followed by the port number that you
want to scan.
nmap 109.74.11.34 -p 21
This
above command will scan TCP port 21 on the specified system. You can
also scan a series of ports by using the -p switch and then listing the
desired ports, separating them with commas.
nmap 109.74.11.34 -p 80,443
This command will scan ports 80 and 443 on the target system. You can scan a sequential range of ports by using the
-p switch followed by the first value in the range, a dash, and then the last value in the range.
nmap 109.74.11.34 -p 0-100
The above command scans the first 100 ports. To scan all 65,536 TCP ports on a target, use the following command:
nmap 109.74.11.34 -p 0-65535
You
can use a TCP ACK scan to identify ports that are filtered. To do this,
use the -sA switch. You can then specify a port or series of ports. No
port specification will scan the standard 1,000 ports. This will then
return a list of filtered ports. An example of this command can be seen
below:
nmap 109.74.11.34 -sA
Penetration
testers and security professionals will sometimes only scan for open
TCP ports on target systems. Overlooking UDP services can cause one to
completely overlook glaring vulnerabilities that might easily lead to
compromise. To scan for UDP services on a target system, use the
following command:
nmap 109.74.11.34 -sU
Because
UDP services are not connection oriented in the same way that TCP
services are, this will take longer than a typical TCP scan. The time
required to complete UDP scans can be reduced by scanning for specific
ports. You can specify ports the same way you had with TCP scans.
nmap 109.74.11.34 -sU -p 69
The above command performs a scan of UDP port 69, a commonly used port for TFTP (Trivial File Transport Protocol). It is also possible to identify the version and version number for each particular service. To do this, use the -sV switch.
nmap 109.74.11.34 -sV
This
command will use a combination of banner grabbing and probe-response
analysis to attempt to identify the service and version number of that
service for each scanned port. Using similar techniques, it is also
possible to have nmap attempt to determine the operating system that is
running on the target. To do this, use the
-O switch.
nmap 109.74.11.34 -O
Once
completed, it will either return a positive identification of the
operating system or it will give a best guess and then a list of other
possible operating systems.
Advanced Scanning Techniques
There
is a common problem that you will frequently encounter when performing a
penetration test against mid to large size enterprise networks. Most
companies and organizations these days have become more security-minded
and will likely have firewalls or intrusion detection systems standing
between you and the systems that you are trying to scan. To scan such
systems, we will need to employ some more advanced scanning techniques.
One way to potentially bypass firewalls and/or intrusion detection
systems is to use some traditional stealth scanning techniques that are
integrated into nmap. One method that can be employed is to use a slower
timing template. Timing templates range from
-T0 (paranoid scan) all the way up to -T5
(Insane scan). The lower the value of the timing template, the slower
the scan will be performed. Slower scans are less likely to be flagged
by intrusion detection systems. An example of a paranoid scan would be:
nmap 109.74.11.0-255 -T0
Another technique that can be used to mask your scan is to flood the network with additional decoy traffic using the
-D
switch. This function will allow you to specify multiple addresses to
spoof traffic from or you can use the RND option to spoof traffic from
random addresses.
nmap 109.74.11.0-255 -D RND:5
In
addition to performing the traditional TCP port scan of the target
systems, the command above will also spoof traffic from 5 random
addresses to obfuscate the actual scan traffic. Another technique that
can be used is to vary the packet length of your transmitted requests.
Some intrusion detection systems and firewalls will drop packets based
on signature packet lengths. To prevent this, you can specify the data
length by using the
--data-length switch followed by the packet size in number of bytes.
nmap 109.74.11.0-255 –data-length 15
This
command will send all scanning traffic in packets that are 15 bytes in
length. While this might be helpful to avoid some signature based
intrusion detection systems, consistently sending packets of an unusual
specified packet length could flag an anomaly based intrusion detection
systems. Network intrusion detection systems will also flag traffic if
you begin to sequentially connect to systems within a specified network
range. To avoid performing your scans in sequence, you can use the
--randomize-hosts switch.
nmap 109.74.11.0-255 –randomize-hosts
This
command above will randomly scan each host in the range instead of
performing them in sequence (109.74.11.0, then 109.74.11.1, then
109.74.11.2, etc…). While you can’t spoof your IP address (because you
wouldn’t receive the replies necessary to determine open ports), you can
spoof your MAC address. To do this, you can use the –spoof-mac switch,
followed by a vendor ID, a specific MAC address, or 0.
nmap 109.74.11.0-255 –spoof-mac 0
Using
0 as your argument will apply a random MAC address to your scan
traffic. One final technique that is worth mentioning is using the -f
switch to fragment packets.
nmap 109.74.11.0-255 -f
Fragmenting
packets will separate the data payloads of your scan traffic into
multiple packets, allowing it to more easily bypass content inspection
intrusion detection systems or firewalls. While all of these techniques
can be effective for scanning publically accessible servers behind a
firewall, they are usually not sufficient for scanning hosts on an
internal network. While certain publically accessible servers will be
available for scanning, much of the internal infrastructure will be
deeper within the network and not so easily accessible. Consider the
diagram in Figure 3. This is a simple example of a common configuration
in enterprise networks.
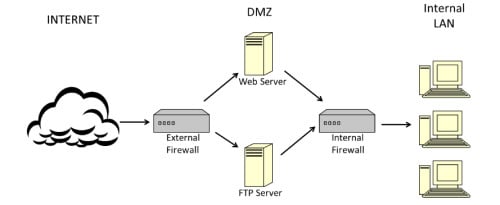
Figure 3. Common Network Configuration
The
problem that we encounter here is that the internal network lies behind
an internal firewall, which has stricter rules about ingress traffic,
compared to the external firewall. This internal firewall is likely
blocking inbound traffic from remote addresses on the web; however, it
is possible that the systems in the DMZ can communicate with the
internal systems. In order to be able to scan these internal systems, we
must make the systems in the DMZ work on our behalf. We will discuss
several different ways to do this, to include proxy scanning, zombie
scanning and FTP bounce scanning.
Probably
the easiest way to scan the internal systems is by using a proxy chain.
Let us suppose that we have acquired access to a proxy service within
the DMZ by locating an open-access proxy service, brute forcing a proxy
service with hydra or by installing a proxy service on an already
compromised machine. Once you have configured your system to route
traffic through that proxy, you can perform nmap scans by using a full
connection scan (
-sT).
nmap 10.1.1.0-255 -sT
If
there is no proxy service available, there are some clever ways that
you can leverage machines within the DMZ to get scan results on internal
systems. One way to do this is to use zombie scanning, also referred to
as idle scanning. In order to perform a zombie scan against the systems
on the internal LAN, we have to find a viable zombie host within the
DMZ. A zombie host is any relatively idle system that uses incremental
IPID sequencing. In order to locate a zombie host, we can use an nmap
script to scan the DMZ for a system that fits this description.
nmap –script ipidseq 109.74.11.0-255
This
script will send a series of packets to each host and track the IPID
numbers for all replies received. It will then analyze these IPID
numbers to classify each system as either random sequence, all zeros, or
incremental. See Figure 4 for an example of the output for an
incremental system.
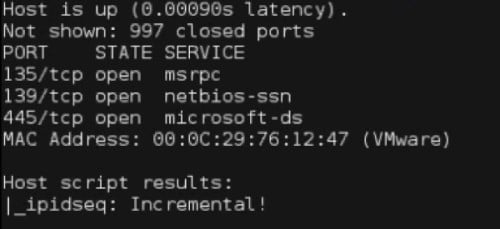
Figure 4. Zombie host located with IPID Sequence Script
Once
we have acquired an IP address for our zombie system, we are ready to
attempt our zombie scan. Prior to addressing how to perform the scan, I
will briefly discuss how the scan works. Refer to Figure 5 for a diagram
of what takes place when a zombie scan is performed against an open
port.
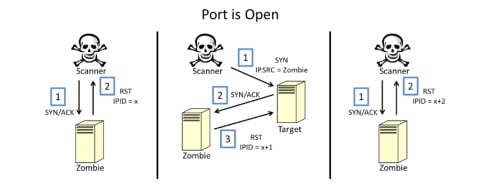
Figure 5. Zombie scan against open port
First,
our nmap scanner determines the current IPID value of the zombie system
by sending an unsolicited SYN/ACK packet. Because no SYN packet was
originally sent by the zombie system to establish a connection, the
zombie then replies to our scanner with an RST packet. Our scanning
system will then use the IPID of the RST packet as a reference point.
Then, our scanning system will immediately follow this up with a spoofed
SYN packet sent to the target system using a source IP address of the
zombie system. Because the source IP address is one within the DMZ, this
connection request is more likely to be able to pass through the
firewall. If the target receives the packet and the destination port is
open, the target will then return a SYN/ACK packet to the zombie system
(who it thinks sent the original SYN packet). Because this SYN/ACK
packet is received out of context, the zombie system will then reply to
the target system with a RST packet, thereby incrementing its IPID value
by one. Finally, our scanner will send one last SYN/ACK packet to the
zombie system. The subsequent RST reply from the zombie will increment
the IPID one more time. So if the targeted port on the remote system is
open, the final IPID value returned will be two numbers higher than the
original value. Alternatively, Figure 6 illustrates what takes place
when the port of the target system is closed.
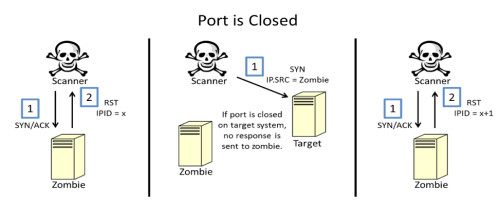
Figure 6. Zombie scan against closed port
If
the port on the target system is closed, the zombie system receives no
unsolicited response from the target and is therefore not instigated to
send an RST packet to the target. So if the IPID value of the final RST
response has only incremented by one, we can deduce that the port is
closed because no SYN/ACK reply was sent to the zombie system to
instigate a RST response. Otherwise, if the final IPID value has
incremented by two from the original value, then we can deduce that the
port on the target system must be opened because it must have replied to
the zombie which instigated the response that incremented the IPID
value of the zombie system.
While
this may sound extremely complicated; do not become intimidated by the
description, as nmap does nearly all the work for you. To actually
perform a zombie scan, you just have to enter a simple command.
nmap -sI 192.168.199.132 -Pn 192.168.199.130
The
-sI switch tells nmap to perform a zombie scan using the following IP address as the zombie host (192.168.199.132). The -Pn
switch prevents nmap from performing an initial ICMP ping on the target
system prior to attempting the scan. So, the final IP address in the
command identifies the target system. The output for this command can be
seen in Figure 7.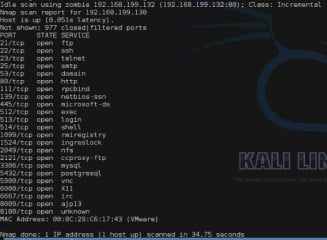
Figure 7. Zombie scan against closed port
It
should be noted that the IP range that I used to demonstrate this
zombie scan is a private range on my internal network. For this to work
effectively against a remote network, as described in the original
scenario, the systems in both the DMZ and the internal network must be
on publically routable IP ranges. If the internal network is configured
on a private range behind a NAT (Network Address Translation)
server, then the nmap scanner will not be able to send the spoofed SYN
packet to the internal address from its remote location.
Another
way to use systems within the DMZ to attempt to scan hosts on the
internal network is to use FTP bounce. Some legacy FTP servers support
the capability of transmitting files to a third party system. If you
have discovered an FTP server in the DMZ that allows anonymous login or
that you have brute forced with hydra, you can test the FTP server to
determine if it supports FTP bounce. To do this, use the ftp-bounce
script.
nmap –script ftp-bounce –script-args
ftp-bounce.username=anonymous,
ftp-bounce.password=bob@gmail.com 109.74.11.201
This
command uses the nmap script with username and password arguments
against the FTP server. Once completed, this scan will indicate if FTP
bounce is possible or not. If the script indicates that FTP bounce is
working, you can use the FTP server to perform a port scan against other
systems on the network. Figure 8 illustrates how this works.
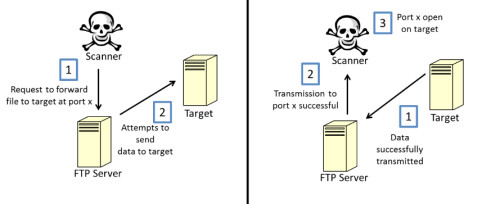
Figure 8. FTP bounce scan
The
scanner will attempt to send binary data, via the FTP bounce function,
to the target system at a designated port. If the data is transmitted,
the FTP server will then report back this back to the scanner,
indicating that the port on the target system is open. To perform an FTP
bounce scan, use the
-b switch.
nmap -b ftpuser:PassW0rd@192.168.11.201:21 10.1.1.128-255
In this command, the
-b function is used to perform a ftp bounce scan using the username “ftpuser” and the password PassW0rd,
against the FTP server at 192.168.11.201 hosted on TCP port 21. The
actions described in the diagram above will then be performed against
each of the common 1000s ports on each of the target hosts from
10.1.1.128 to 10.1.1.255.
Vulnerability Mapping and Exploitation with NSE
Once
you have discovered live hosts on the target network and have managed
to enumerate open ports and/or running services on those hosts, you can
begin testing for and exploiting vulnerabilities. With the newly
integrated NSE (Nmap Scripting Engine), there are a number of preloaded
scripts that come with the standard nmap installation. These scripts
have a wide range of different functions from basic information
gathering (like the two that we have already discussed), vulnerability
mapping, brute forcing, denial of service and even remote exploitation.
All of these scripts are located in your nmap installation directory. In
Kali-Linux, they can be found at
/usr/share/nmap/scripts/. To browse to these scripts and begin working with them, use the following commands:
cd /usr/share/nmap/scripts/
ls
The
cd command will change the directory to the location of the NSE scripts, and the ls command will display the contents of the directory. You can then view any of the scripts by using the cat command, followed by the name of the script that you want to view. For the purpose of this demonstration, we will use ftp-vuln-cve2010-4221.nse. To view the contents of this script, use the following command:
cat ftp-vuln-cve2010-4221.nse
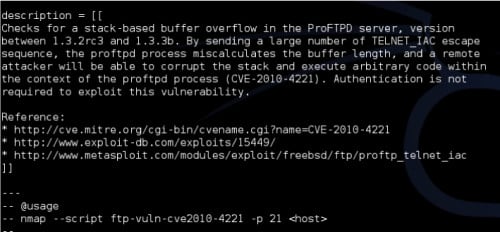
Figure 9. NSE script contents
Figure
9 displays the contents of this script. If you browse to the top of the
script contents, you will see several pieces of helpful information to
include a description of the script, a list of additional resources for
reference, and appropriate use and syntax of the script. However,
sorting through these scripts in the directory and locating a script
that performs a specific function can be very tedious. In my opinion,
this is where Zenmap (the graphical interface that we had previously
discussed) really shines through. To demonstrate how helpful the Zenmap
interface can be when working with NSE scripts, open it once again from
the command line with the command:
zenmap
Then
select the Profile drop-down menu and click “New Profile or Command.”
After the Profile Editor opens up, choose the Scripting tab at the top
of the screen. Figure 10 displays an image of the Zenmap Scripting
interface.
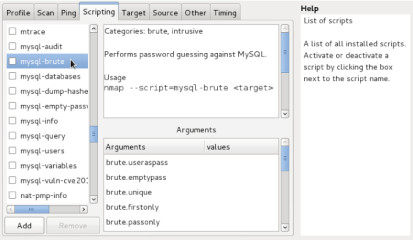
Figure 10. Zenmap Scripting Interface
A
list of all of the available nmap scripts is located on the left side
of the screen. You can select any of these to have it included in your
nmap command. Some scripts will require arguments in order to be able to
run correctly. Post authentication scripts will often require a
username and password for specific network services. In the example in
Figure 10, arguments can be supplied to configure the brute force attack
that is to be performed against the MySQL service. You can also easily
pass the script arguments by entering the values in the Arguments
window. These arguments will automatically be populated in the generated
nmap command. The window in the top center provides a description of
the selected script, appropriate use and syntax, and even categories to
describe the functions of the script. These categories can be especially
helpful if you are trying to perform a specific type of task, such as
vulnerability analysis. After launching an NSE script with an nmap
command, you will see the results in the standard nmap output. In the
case of brute force scripts, the output will show if the brute force
attack was successful and, if so, will display the discovered username
and password. In the case of vulnerability scripts, the output will
indicate if the vulnerability is present on the target system(s). And in
the case of exploitation scripts, the output will provide information
about the payload that was subsequently delivered to the target system.
Scripting with Nmap
In
addition to its own integrated scripting engine, nmap also supports
several output options that make it easy to use traditional scripting
languages for performing output analysis. Two output formats that can be
useful for scripting include greppable output (
-oG) and XML output (-oX).
XML can be effective for higher level scripting languages that have
modules that can be imported for XML parsing and greppable output can be
used in conjunction with the bash shell scripting to streamline
analysis of nmap results. To demonstrate how this output feature could
be used in conjunction with scripting, we will review a simple 4-line
bash shell script, displayed in Figure 11 to analyze the results of an
nmap scan.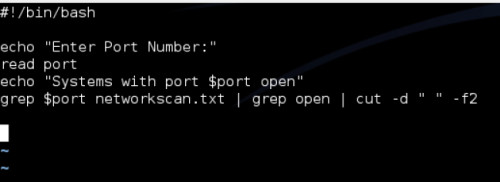
Figure 11. Nmap Result Analysis Bash Script
Consider
a scenario in which an nmap scan was already performed against a very
large network and the output of the scan was saved in greppable format
to a networkscan.txt file. And suppose that we want to use hydra to
perform a brute force attack against all FTP services on the network,
but we do not want to waste the time that would be required to scan port
21 on the entire network again. This simple script will extract all
systems that have a specified port open. The first line prompts the user
for a port number. The second line then assigns the value of the user
input to the ‘port’ variable. The third line indicates to the user that
all systems with that open port will be listed. And finally, the last
command is where we grep out the results from the nmap greppable output.
The script uses the grep command to extract all lines from the output
file that reference the specified port. This will include lines that
enumerate each instance of where the port is open, closed or filtered.
Then, it pipes that output over to another grep function that extracts
only instances in which the specified port is open. This output is then
piped over to the cut function, which specifies a space character as the
delimiter and then outputs the second field. By doing this, our script
then outputs the IP address for each system that has the specified port
open. Figure 12 displays the output of the script.
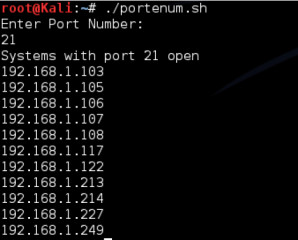
Figure 12. Nmap Result Analysis Script Output
While
this is a very simple script, it demonstrates how easy it can be to
extract information from the greppable output format. Once acquired,
this collected information could easily be used for further scripting.
It could be used as a starting point to perform some other subsequent
task against each system that was identified to have a specific port
open.
An All-In-One Penetration Testing Tool
By
combining its different capabilities, one could easily perform a
complete penetration test by using nmap alone. There is no denying that
nmap, with its impressive list of functions and capabilities, is a truly
powerful tool. And as the years progress, it will likely become even
more powerful as more people continue to contribute to this project.
Like a kid with his father’s gun, nmap can be a dangerous tool in the
wrong hands. But if used correctly, it can be an invaluable asset for
ensuring the security of your network infrastructure. So always remember
to use it wisely and to use it well.
No comments:
Post a Comment