Maltego
is capable of gathering information about either a network or an
individual; here we will focus on the former and leave individual
information gathering for another time. We will be looking at gathering
info on all the subdomains, the IP address range, the WHOIS info, all of
the email addresses, and the relationship between the target domain and
others.
Let’s start by firing up Kali and then opening Maltego. Here is a complete tutorial about hacker's OS Kali Linux, so read this before you go ahead: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
When you open Maltego, you will need to wait a brief moment for it to startup. After it finishes loading, you will be greeted by a screen asking you to register Maltego.
Go ahead and register and save and remember your password as you will need it again the next time you login into Maltego.
After successfully registering and logging into Maltego, we will have to decide what type of “machine” we want to run against our target. In Maltego’s parlance, a machine is simply what type of footprinting we want to do against our target. Here, we are focusing on the network footprinting, so our choices are:
Let’s choose an L3 footprint that will gather as much information as we
can; this is also the most time-consuming option, so be aware of that.
Now, that we have chosen a type of machine for our footprinting, we will need to choose a target. Let’s choose our friends at SANS, one of the leading IT security training and consulting firms in the world.
Now, click “Finish” and let Maltego do its work.
Maltego will now begin to gather info on our target domain, sans.org, and display it on screen. In the screenshot below, we can see that Maltego has already collected the email addresses from the site, while it collects the nameservers and mail servers.
Finally, we can click on “Bubble View” when Maltego is done and see all of the relationships between our target and its subdomains and linked sites.
Click on new icon (see image) for gathering the information
By clicking left button of mouse drag the domain in Main view.
Double click on domain icon and rename it into your target domain. Here I am taking google.com as example.
Here we are searching for top level domain for our target domain. First right click on domain then
Run Transform → All Transforms → To Domain ( Find other TLDs)
Here we got the result of TLD search.
Now we are to gain more information about these domains. First of all select all domains by dragging left mouse button or you can select one by one press Shift + left click.
After selecting all domains, right click one of them and then
Run Transform → All Transforms → To Website (Quick-Lookup)
Here we are going to search all website which are associate with these domains.
Well here we are just replacing the a website icon I have targeted http://www.google.com for more info follow the image. This is not a necessary part but you should learn it.
Here we are going to find the IP address of our target website. Right click on target website then
Run Transform → Resolve to IP → To IP Address (DNS)
Here we got the IP address of our target website and the detail of where its located.
Step 1: Open Maltego & Register
Let’s start by firing up Kali and then opening Maltego. Here is a complete tutorial about hacker's OS Kali Linux, so read this before you go ahead: An Introduction To Hacker’s OS: Kali Linux Setup Tutorial
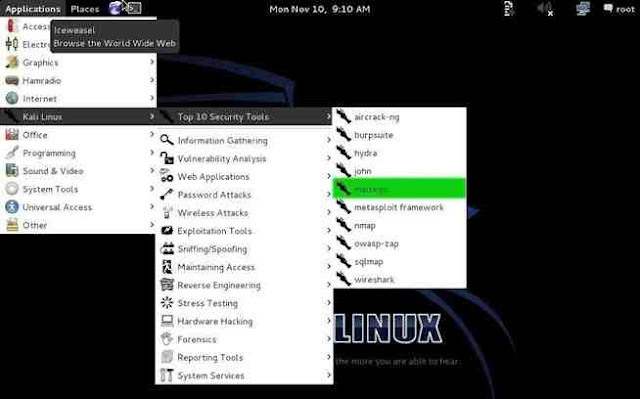
Maltego can be found in numerous places in Kali, but the easiest way to get to it is to go to Applications -> Kali Linux -> Top 10 Security Tools. Then, among the Top 10, you will find Maltego at number 5, as shown in the screenshot below.

When you open Maltego, you will need to wait a brief moment for it to startup. After it finishes loading, you will be greeted by a screen asking you to register Maltego.
Go ahead and register and save and remember your password as you will need it again the next time you login into Maltego.
Step 2: Choose a Machine & Parameters
After successfully registering and logging into Maltego, we will have to decide what type of “machine” we want to run against our target. In Maltego’s parlance, a machine is simply what type of footprinting we want to do against our target. Here, we are focusing on the network footprinting, so our choices are:
- Company Stalker (this gathers email information)
- Footprint L1 (basic information gathering)
- Footprint L2 (moderate amount of information gathering)
- Footprint L3 (intense and the most complete information gathering)
Step 3: Choose a Target
Now, that we have chosen a type of machine for our footprinting, we will need to choose a target. Let’s choose our friends at SANS, one of the leading IT security training and consulting firms in the world.
Now, click “Finish” and let Maltego do its work.
Step 4: Results
Maltego will now begin to gather info on our target domain, sans.org, and display it on screen. In the screenshot below, we can see that Maltego has already collected the email addresses from the site, while it collects the nameservers and mail servers.
Finally, we can click on “Bubble View” when Maltego is done and see all of the relationships between our target and its subdomains and linked sites.
How to find IP address
By clicking left button of mouse drag the domain in Main view.
Double click on domain icon and rename it into your target domain. Here I am taking google.com as example.
Here we are searching for top level domain for our target domain. First right click on domain then
Run Transform → All Transforms → To Domain ( Find other TLDs)
Here we got the result of TLD search.
Now we are to gain more information about these domains. First of all select all domains by dragging left mouse button or you can select one by one press Shift + left click.
After selecting all domains, right click one of them and then
Run Transform → All Transforms → To Website (Quick-Lookup)
Here we are going to search all website which are associate with these domains.
Well here we are just replacing the a website icon I have targeted http://www.google.com for more info follow the image. This is not a necessary part but you should learn it.
Here we are going to find the IP address of our target website. Right click on target website then
Run Transform → Resolve to IP → To IP Address (DNS)
Here we got the IP address of our target website and the detail of where its located.










No comments:
Post a Comment